Apple Base Station Encryption Options
Cost and Benefit of Encryption
Encryption is a means for wireless networks to acheive some semblance of security... as the encryption algorithms used by industry may not be perfect but will keep most casual hackers out of your network. Network security is very important not only to prevent others from hacking into your machines, but also to prevent them from launching attacks on internet-based machines from your access point. For when the authorities trace a attack back to its origin, it's your access point or base station that will be referenced. In other words, your access point may give attackers not only a free and fast connection to the 'net, it'll also make you potentially liable for the damages.
One particularly egregious example of these risks involved a Canadian suspect who was allegedly caught downloading child pornography with his pants around his ankles while sitting in a car outside an unsuspecting home. If the man had not been caught, the owner of that access point could have been fingered by the server logs later on... Other examples of security breaches include "drive-by" virus infections, where infected mobile laptops spread their payloads into open networks. etc. In other words, network security should be practiced assiduously.
On the other hand, most governments do not like encryption for anyone but themselves... to make snooping on citizens easier. Hence, the pressure on manufacturers to make encryption relatively easy to crack... Only in the year 2000 did the US government finally allow encryption keys with up to 128 bits to be used domestically and to be exported to friendly countries. See this link for more information on the cryptographic stances of countries around the world.
When wireless access points were initially developed, the various manufacturers agreed to a common encryption standard to ensure interoperability and security. The first standard to be developed was called "Wired Equivalent Protection" (WEP). The name implies that a WEP-enabled network is as snoop-proof as a physical network consisting of CAT5 wires, etc. Within two years, researchers at several universities broke this encryption method with statistical attacks due to deep flaws in the implementation of WEP.
As the WEP encryption algorithm was kept secret and no peer review by the cryptographic community was allowed, perhaps its not too surprising that the algorithm is flawed... yet another instance of practicing a tired art known as "security through obscurity". Such "security" is actually quite dangerous as it gives users a false sense of safety.
Anyway, WEP comes in several key lengths, ranging from the 64bit-long keys used in Graphite base stations all the way to 256bit keys used for some non-Apple hardware. Assuming you have a robust encryption algorithm,the longer the key length, the more secure your transmission will be. However, due to the inherent algorithm weaknesses WEP is vulnerable, regardless of key length to statistical attacks that exploit said weakness. Note: Research into such algorithm vulnerabilities is now illegal in the USA thanks to the DCMA act. Please support organizations like the Electronic Frontier Foundation to help repeal laws like the DCMA act that do far more harm than good.
Given WEP's obvious vulnerabilities, does this mean that WEP should not be used? Not at all, because any security is better than nothing. It's a bit like having an older Kryptonite bicycle lock securing your bike (which can be broken in 15 seconds or less with a Bic pen). While being relatively easy to bypass, the Kryptonite lock may make casual thieves move on to easier targets. WEP can provide more robust protection than that (it takes longer break WEP networks) and 128bit WEP is usually good enough for residential applications.
In response to the black eye caused by the inadequacies of WEP, several equipment vendors came up with more secure solutions, most notably the Light Extensible Authentication Protocol (LEAP) developed by Cisco. These improvements were rolled into a new standard called "WiFi Protected Access" (WPA). WPA cycles the vulnerable portions of the WEP keys pretty quickly, making statistical attacks a matter of hours or days instead of minutes. Such protection is usually good enough for most commercial and all residential applications. Hence, I would use WPA encryption whenever possible.
As of Airport 3.3, WPA is available for all Apple computers with any kind of built-in "Airport" card running OSX 10.3 and higher. Even external PC and PCI cards with the 802.11g BroadCom chipset in them are supported natively (see my buying guide). If you desire the best security, WPA is the way to go. The only major drawback is that older computers (i.e. pre-OS X 10.3) will not be able to connect. Even Windows XP computers can take advantage of WPA now.
However, encryption does not come without a price. It significantly increases the overhead and bandwidth associated with routing LAN traffic, as every packet of information flowing between the access point and an attached device has to be encrypted. Depending on your access point and connection to the internet, the performance of your wireless LAN can suffer accordingly. For example, the first generation Apple Base Station (a.k.a. "Graphite"), suffers from 3x performance degradation whenever WEP is turned on. More modern base stations (Snow, Extreme, Express) have better CPUs so their performance suffers less due to enabling encryption but the additional bandwidth requirements stay the same.
You can enable WEP/WPA encryption on all base stations by clicking on the "Change Wireless Security" button found on the Airport Tab in the Apple Admin Utility (instructions for "Graphite" (OS 9 or OS X), "Snow", "Extreme", and "Express" base stations). Here are some recommendations by base station model:
Graphite Base Station:
Graphite Base Stations were developed at Lucent before the US government allowed more robust encryption standards to be exported. Hence, it only features 64bit WEP, which is the oldest WEP standard, and the easiest to break (usually in seconds). Due the crushing performance hit associated with enabling WEP, I would only consider using this form of WEP if you use the base station with dial-up telephone connections. Here, the connection speed is so slow that you won't notice the performance hit. Any connection to the internet via the ethernet port (i.e. "high speed") is better secured by other means, like Access Control and careful antenna/base station placement.
Theoretically, 128bit encryption is possible on "Graphite" base stations, if you retrofit a 128bit capable "Classic Gold" Orinoco (or Lucent WaveLAN Gold) PCMCIA card into your base station and then use a non-Apple configurator to set it up (the Admin Software won't). In other words, this is a lot of trouble for very little reward. I'd buy a new Linksys router or an Airport Express before going through all that trouble, just to end up with a hard-to-administer and slow base station.
The security of the WaveLAN Silver card found inside "Graphite" base stations can be "upgraded" by extracting the card, sticking it into a non-Airport laptop, and installing the latest Airport software under OS 9 as described here (thanks Winston Weinmann!). However, the new firmware does not allow the use of 128 bit encryption when the card is re-inserted into the ABS - only a 10 byte key is generated, not the 13 byte key characteristic of later cards.
Snow Base Station:
128bit WEP made its introduction on Apple hardware with the "Snow" base station. Apple allows all of its 2nd generation "Airport" PC cards to be upgraded to 128bit WEP via a firmware upgrade that the Apple hardware does as part of installing the most recent Airport software. As 128bit WEP is fairly effective and widely-supported, I would enable it on all Snow base stations.
Extreme and Express Base Stations:
Starting with version 3.3 of the Extreme base station firmware, Apple introduced "Personal WPA" encryption on on the Extreme and Express base stations. Only computers running OS 10.3, Windows XP SP2, or later can use WPA. OS9 computers are limited to WEP. Even external PC cards with the 802.11g BroadCom chipset in them are supported natively (see my buying guide). Thus, if every computer on your network can support WPA, this is the standard I would select. Otherwise, opt for 128bit WEP.
Enterprise WPA
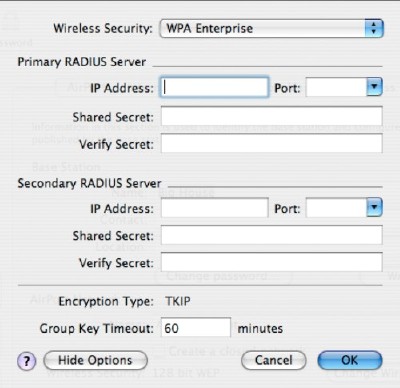
Enterprise WPA is basically a RADIUS and LEAP implementation for businesses. It allows an administrator to change keys throughout the wireless network simultaneously and quickly. Home owners are unlikly to have a RADIUS server lying around, so this feature is usually only found in commercial environments.
Enterprise WPA is very similar to Personal WPA except that it's possible to fine-tune more aspects of the ABS behavior, controlling the key-swapping via central servers. If you have a functioning RADIUS server and the desire to put it to use, the first order of business is to enter the IP addresses of your primary and secondary RADIUS servers, along with the ports that the ABS is supposed to communicate with.
Next, enter the shared secrets for both systems and you're done. If you click on the "Show Options" button, you'll be presented with a dialog that allows you to chose how quickly the vulnerable keys are swapped. Since breaking 128 bit WEP encryption usually takes several hours on a busy network, leaving the default 60 minute value should be pretty safe.
Enterprise WPA can only be used by machines and base stations that understand WPA also. Thus, only "Extreme" and "Express" base stations can be part of such a network.
Other Encryption Options
I would also seriously consider other forms of encryption, depending on how you use your network. Commercial users of wireless networks ought to upgrade their infrastructure to WPA (i.e. Extreme, Express, or equivalent access points) as quickly as possible. This will usually protect your network adequately. However, you also ought to think about outside resources when it comes to encyrption and security
For example, most of us use mail servers on the internet to get and send our e-mail with. In the early days of the internet, the POP and SMTP mail transfer protocols were developed to facilitiate mail transfer. However, neither of the two is protected by encryption, causing all mail transfer to occur in plaintext. Not only can any machine on the same network read your e-mail while it is being transferred, worse, it can read the login and password as well.
Thus, I would consider some of the readily-available tools to make mail transfers more secure. The easiest means (if supported) is using Secure Socket Layers (SSL), the same mechanism that secures many on-line credit card transactions. Most e-mail clients have a check box to turn this functionality on with, and most mail servers allow SSL connections as well.
Even better, by using SSL-enabled e-mail connections, you bypass the ports that many ISPs routinely block to battle the spread of Spam. Ports are like the gatehouses found in old walled cities, where each port is typically reserved for a particular service, like Port 25 is reserved for the SMTP mail transfer protocol. Since many virii and trojan horses have built-in mail servers, many ISPs have disabled port 25 and only allow connections to their own SMTP servers... but as the SSL-enabled SMTP connection uses port 465, you bypass this problem altogether. Try it, the worst thing that can happen is that it doesn't work...
Those of us that run web-servers with a myriad of services may use SSL or opt for SSH tunnels instead. I happen to use SSH tunnels to secure my e-mail, file transfer, etc. so that I can connect to my server from any access point in the world without worry. While there is a cost for personal SSL certificates, SSH connections (where supported) are free, but harder to implement. Thus, I recommend SSL for its ease of use to most home users while reserving SSH for the power users that need additional functionalities at zero cost.
Passive means to improve wireless LAN security
A passive means of increasing security is through the use of "sector" antennas instead of omni-directional ones. For example, you can set up a sector-antenna at the edge of the building to face inwards and away from any adjoining roads. Any hackers roaming the neighborhood will subsequently have a much harder time picking up your signal. See my Antenna discussion page for more information.
If you came here from one of the Configuration guides, here are some links to get back to the Airport Tab pages for each base station:
- "Graphite Base Station" (OS 9 or OS X)
- "Snow Base Station"
- "Extreme Base Station"
- "Express Base Station"
